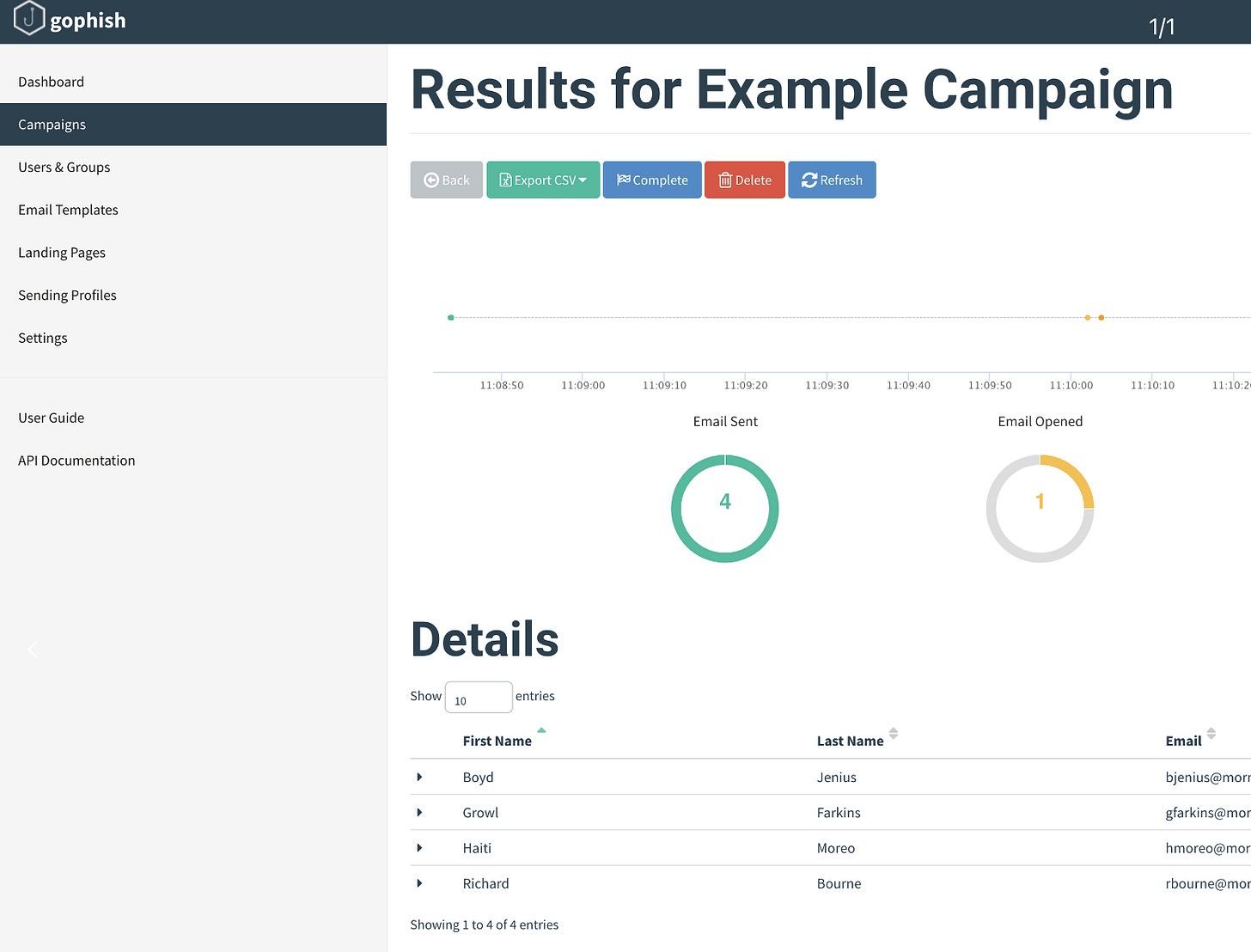
How to find a phishing websites of your company
The cycle of articles how to find phishing websites for your company and – how to protect of them (blocking techniques)
All these actions are significant, especially for financial institutions
The problem
A hacker can create a clone of your website
There are many tools to automate this action, for example:
Gophish - “is a powerful, open-source phishing framework that makes it easy to test your organization's exposure to phishing”
Tools like Gophish automate:
Clone your website
Send email campaign
And collecting data (login/paswords)
Below I’ll describe several ways how to find these clones automatically or manually
Canary tokens by Javascript
Javascript canary token is a script like this:
if (document.domain != 'company.com') call() Just remember:
automation tools like Gophish will replace your website address (company.com) in the content with a phishing domain
that is why very important to convert domains to base64 or calculate and use a hash value
the
call()function should create the<img>tag withsrcattribute containing your particular backend and current domain name (why <img> – it’s the reliable way to do a cross-domain request)
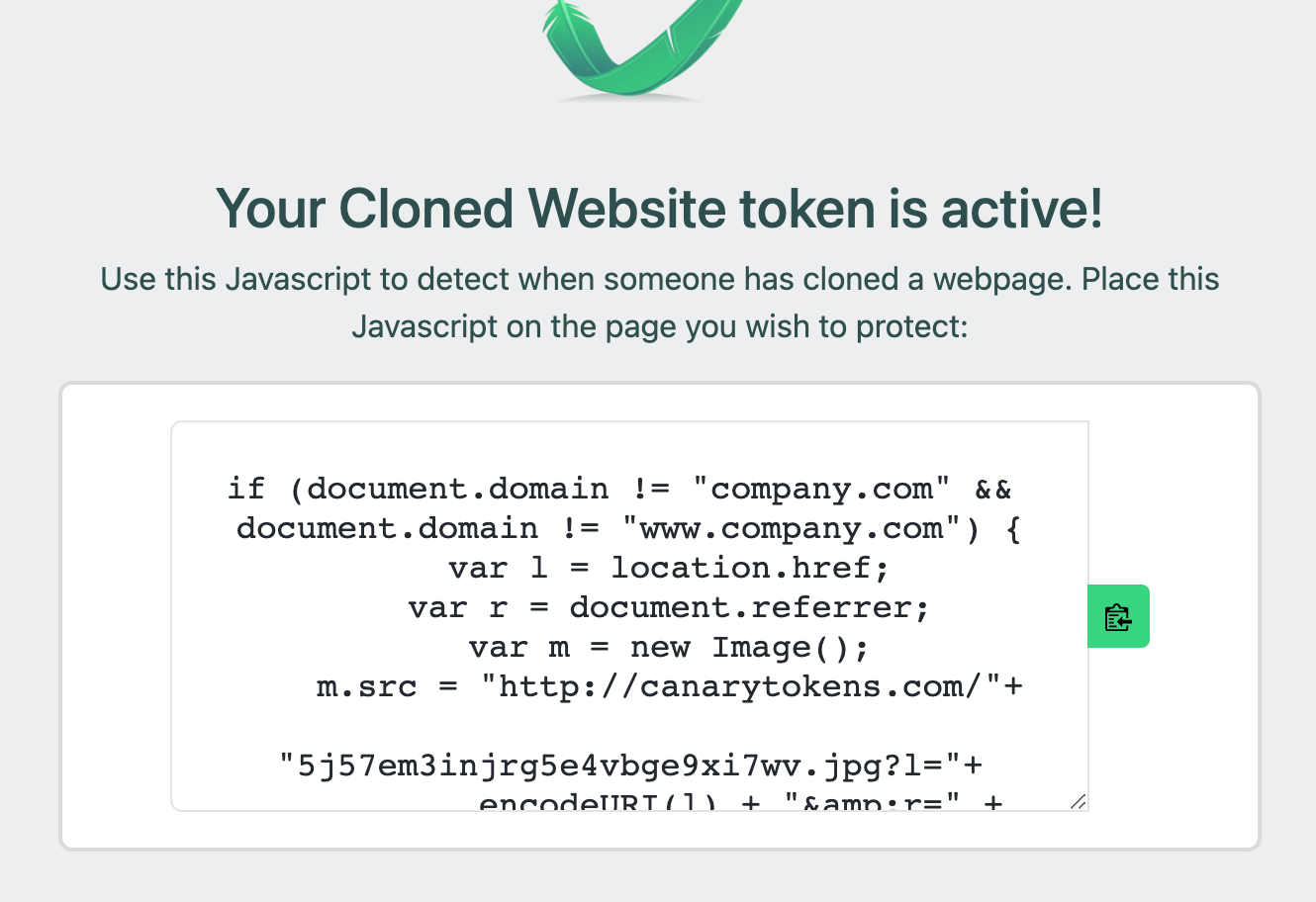
A good start – to use https://www.canarytokens.org/
As a result, you will receive a script:
if (document.domain != "company.com" &&
document.domain != "www.company.com") {
var l = location.href;
var r = document.referrer;
var m = new Image();
m.src = "http://canarytokens.com/"+
"5j57em3injrg5e4vbge9xi7wv.jpg?l="+
encodeURI(l) + "&r=" + encodeURI(r);
} You may use it as is, but again – try to replace your domain with something calculated
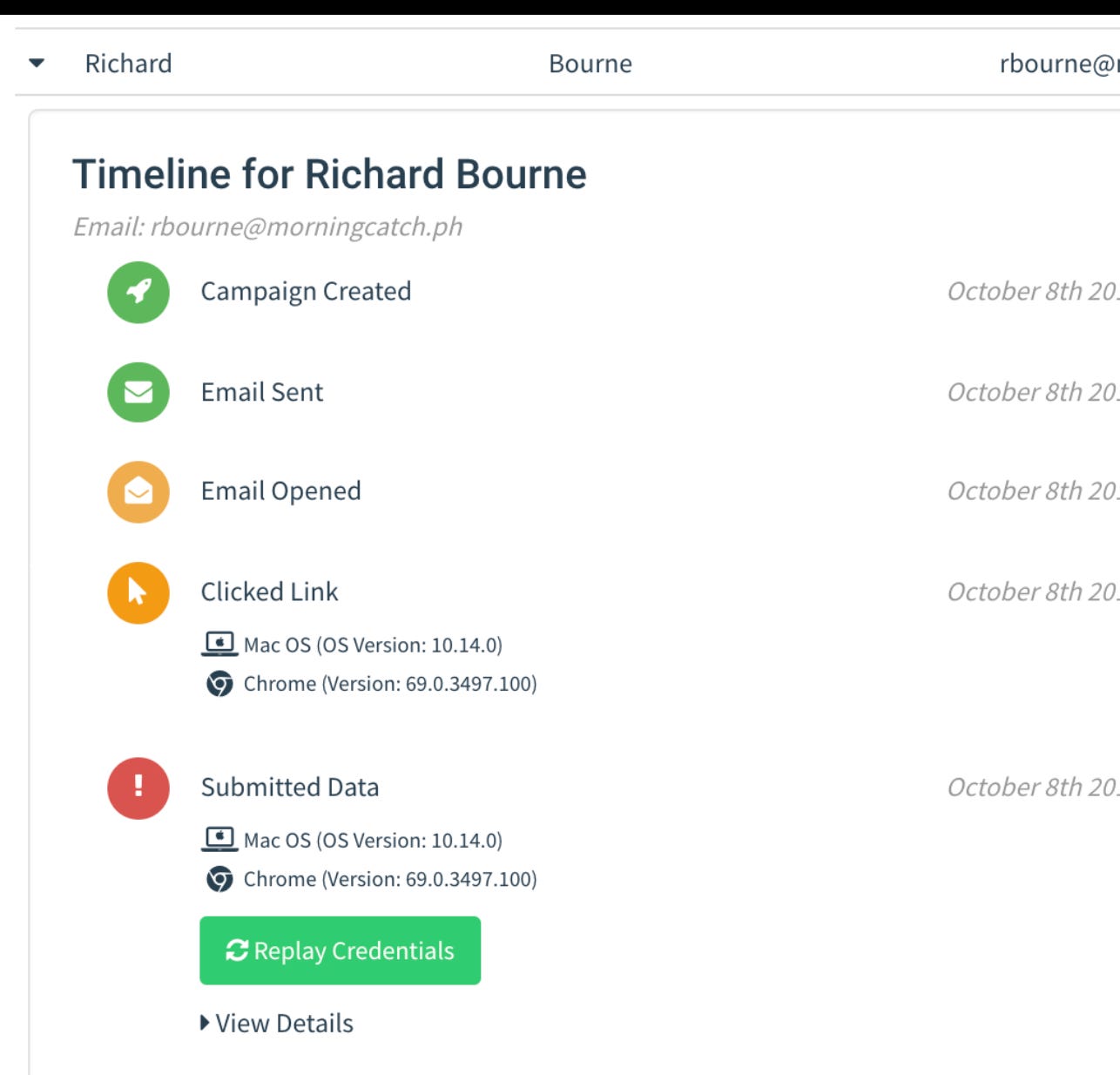
When this script proceeds on the cloned/phishing website you will receive an email notification (with the IP address of the potential victim or attacker)
Canary tokens by Referer header
The Referer HTTP header is a special header that passed to web servers with origin url
For example, somebody cloned your website and deployed it on login-company.com
If your website contains an image with a full path to //company.com/img.png – the phishing website will request this URL with its web-URL
So – turn on logging of all referer requests to your website
And you just need to configure alerts for cases when your web server receives unexpected referees headers
Of course, phishers may configure Referrer-Policy with value no-referrer, but in most cases – they don’t
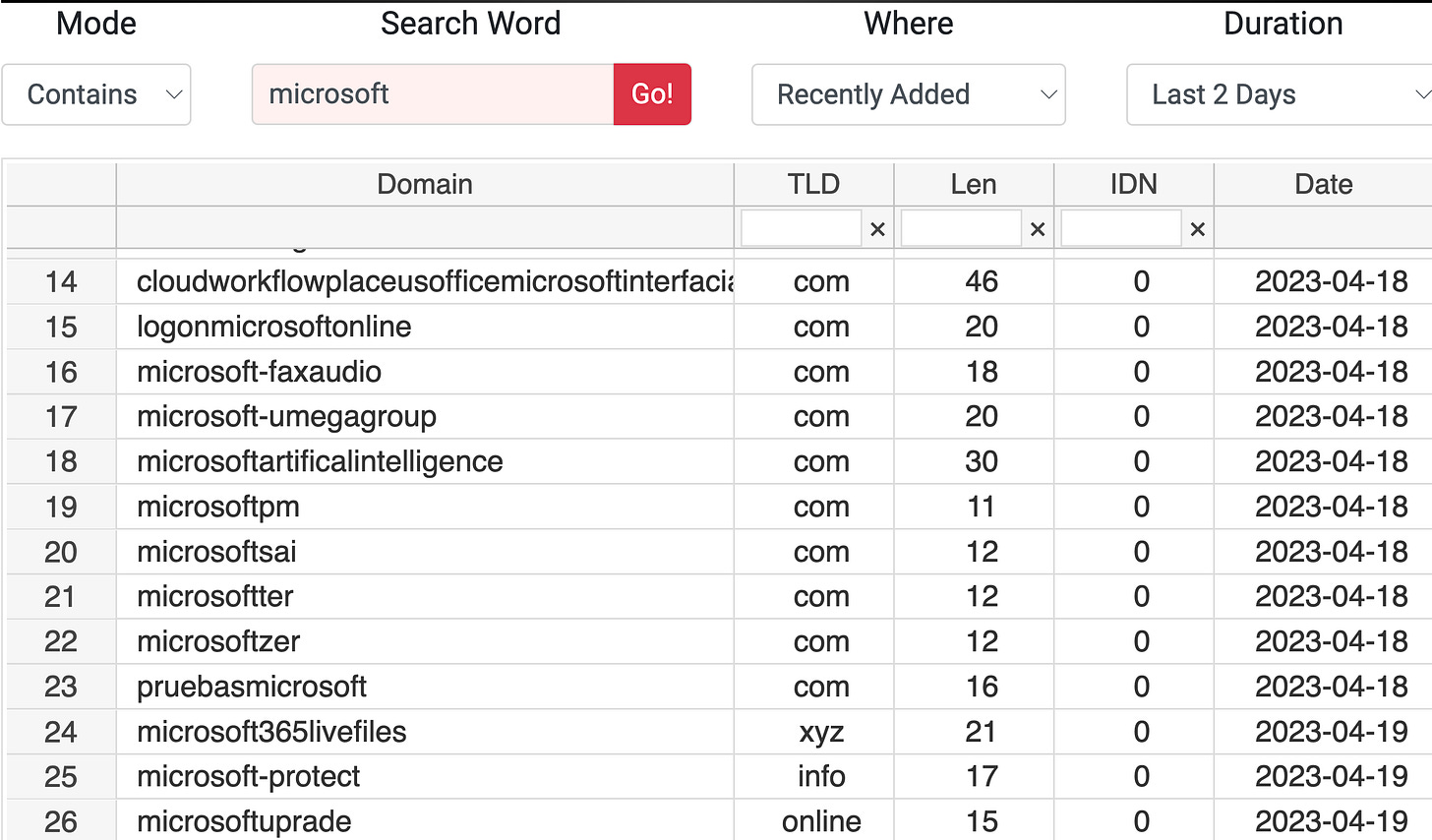
Research recent domains
At least you may monitor a recent DNS activity, try it with your company website address/name here https://dnpedia.com/tlds/search.php
do not forget to try to replace the letter i by l, or l by 1 (looks similar?)
or i can be replaced by the Greek ί, etc…
Ok, it is a short intro, next time I’ll talk about what to do when you will find phishing resources, and later - how phishers find victims